Identity Framework
Building the identity play to level up your skills of Self-Sovereign Identity
An immense amount of information exists over the Internet for the self-sovereign identity (SSI) - good enough to get lost. I have created an identity lego structure that will provide a context when I publish the information related to SSI. Initially, this could be overwhelming, but let me ensure that it will get palatable and exciting.
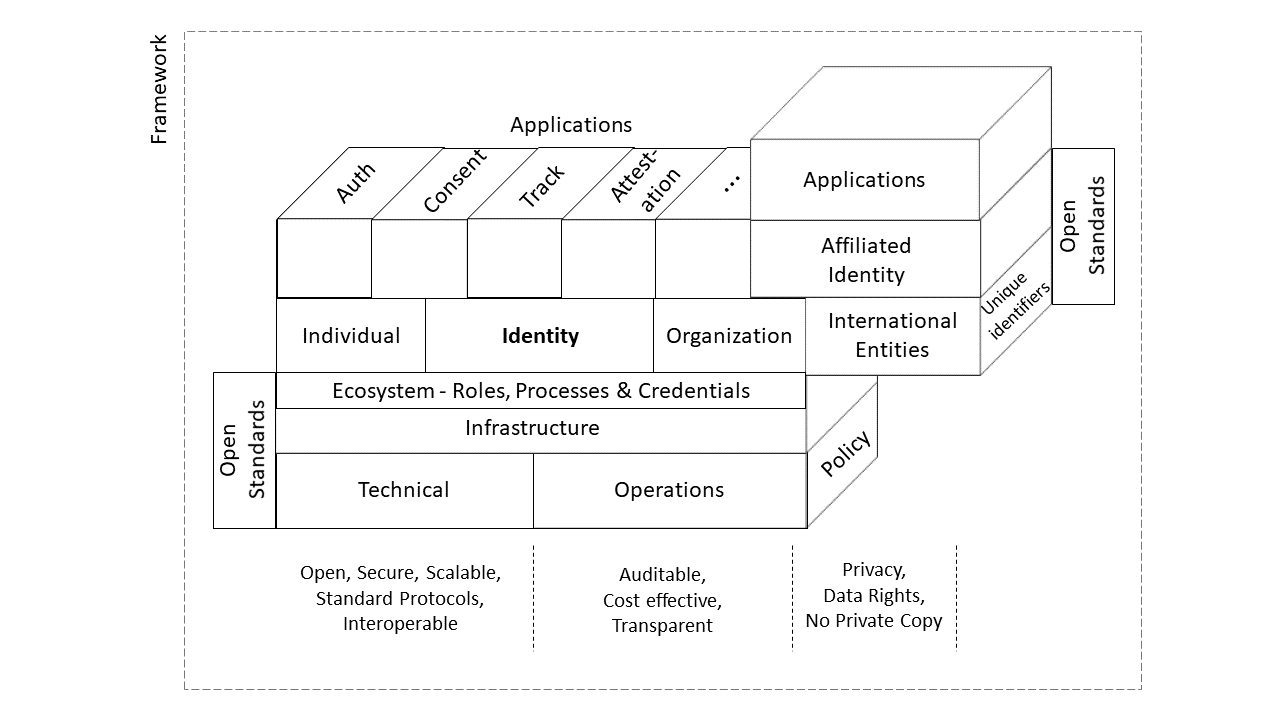
Some of the frameworks have extensively and exhaustively captured the specific areas; however, I have laid out this framework abstracting those areas with the base infrastructure at the bottom and building upon it towards the applications at the top layer, and at the heart of this framework is Identity. The Decentralized ID (DID), and ecosystem roles, processes and verifiable credentials are inspired by W3C Recommendation and the Pan-Canadian Trust Framework (PCTF).
Infrastructure
The PCTF identified three enablers on technical, operational and government policies that are essential for creating any meaningful self-sovereign identity framework with any jurisdiction boundaries.
Technical enabler leads towards secure, scalable and interoperable solutions using standard protocols across various sectoral or jurisdiction boundaries. Operational enabler ensures transparent, audible and cost-effective infrastructure setup. The government policies are critical drivers for user privacy and data rights to protect identity data being copied over without user consent.
Ecosystem - Roles, Processes & Verifiable Credentials
The digital ecosystem defines roles and the information exchange processes among these roles to issue, store, request, present, recognize and verify verifiable credentials.
W3C has generalized actors into three critical roles, and their actions are mentioned under their name.

Issuer: The authority whose identity is well-known and can issue verifiable credentials to the holder.
Holder: The holder can acquire, store and present verifiable credentials. In the case of minors (precisely calling them as subjects), parents can act as holders.
Verifier: The verifier can request and verify verifiable credentials based on information (identifiers and schema) present in the credential.
Verifiable Data Registry: The registry holds information about the identifiers, the credential vocabulary (Citizenship vocabulary example found here) and schemas associated with verifiable credentials.
Verifiable Credentials
These are the digital claims made by the issuing authority for the subject’s identity or specific properties or attributes they possess. W3C published Verifiable Credential specification 1.0 recommendation is extended to divide this further into the Verifiable Presentation part taking university degree as an example.
Verifiable credentials represent all the same information that a physical credential represents with digital signatures embedded in it to make them tamper-proof and more trustworthy.
The primary use case of verifiable credentials is for person and organization identity now. However, it’s possible to represent the physical world goods, IoT devices and software systems digitally using verifiable credentials with its vocabulary and schema.
Identity
The digital identity is the representation of a real person alive or dead, or a legally registered organization active or inactive. The digital representation of identity allows these actors to consume services built on top of the digital ecosystem internally or exposed from other players.
Person
Person identity is created when a person is born, immigrated or visits the country in the form of birth certificate, passport, landing paper, or visa. This government-issued identity serves as a foundational identity to provide further services and new derived identities, which will be described in Affiliated identity.
Organization
Organization identity is created when an entity is registered with the federal or provincial government to represent sole proprietorship, partnership or corporations, including not for profit. The organization's identity is connected and related to its employees and goods or services they produce.
Affiliated Identity
When a person goes to school or works for an organization, the school or organization services are consumed through the issued Student ID or Employee ID. This affiliated identity can be linked back to their foundational identity.
Moreover, the organization can attach an affiliated identity to robots (physical/software agent), or to physical goods by issuing verifiable credentials. International entities like GS1 issues unique number which can be affixed on physical goods and embedded into verifiable credentials. This affiliated digital identity is useful, mainly when these robots act as financial advisors or ethical AI algorithms or tracing goods.
Open Standards
W3C Credential Community Group (CCG) has been continuously striving for open standards, and their tremendous efforts have culminated in two most important recommendations for setting up the groundwork moving towards decentralized identity.
Open, Secure, Scalable and Interoperable standards are keys for any technology or framework to be successful. The above recommendations have the right ingredients for open participation and innovation.
Applications
SSI allows creating interesting applications, and some of the visible benefits are mentioned below.
Authentication/Login
The user does not need to remember all those usernames and passwords if SSI gets integrated into any Web/Mobile applications.
Consent Management
The user is able to provide on-the-fly or time-period-based consent to a person or organization.
Track/Tracing Goods
The supply chain networks can harness the power of SSI to track goods and products effectively.
We will explore these use cases further in future issues.
International Entities / Unique ID
Serial numbers, barcodes, QR codes, etc. are part of our daily life. These unique IDs are the result of consolidated efforts of the industry to standardize and recognize across geographical boundaries. I have included such International entities here in the framework to link those unique IDs back with their digital representation.
The not-for-profit entity like GS1 produces unique numbers for identifying products, data synchronization networks, document types, locations, shipments and many more. The organizations use these unique numbers to embed, print or inscribe on their physical products.
ISCC defines identifiers for any digital content like text, image, audio and video.
When this unique ID interweaved within the verifiable credential product or content schema and tracked along with the physical product or digital content, it helps to build more robust and tamper-proof applications of trust.
Summary
I have created a self-sovereign identity framework and its key components briefly above. We will delve into the individual components and layout its role more clearly in subsequent issues.
Additionally, I have quoted from the PCTF framework. There are other frameworks in place, and one notable is from the Financial Action Task Force (FATF).
Actions
Save or print the framework
Grasp the understanding of mentioned components
Read through those embedded links
All content free now. Subscribe by email so that you do not miss any article.
This post and the information contained herein is provided for informational and discussion purposes only.
