The identity space has evolved from centralized identity providers to user-centric identity over a period (we will go in detail in a future article); however, today, we would like to focus on some of the guiding principles of Self-Sovereign Identity.
“The user must be central to the administration and control of their identity”
We will be zooming in on - the heart - Identity piece today from our Identity Framework that can be found here if you have missed it. We will also explore applying these principles to the identity of an organization or a thing.

Back in 2016, Christopher Allen, a technologist, devised ten guiding principles for Self-Sovereign Identity after consolidating some of the earlier work. In his article, he has meticulously captured the evolution of SSI from the initial work of Moxie Marlinspike, a developer, as a mathematical policy to a legal policy in the Open Identity Exchange (OIX) trust framework by Respect Network.
For ease, I have categorized those ten principles in three major areas - an admin group, a security group and a mobile group.
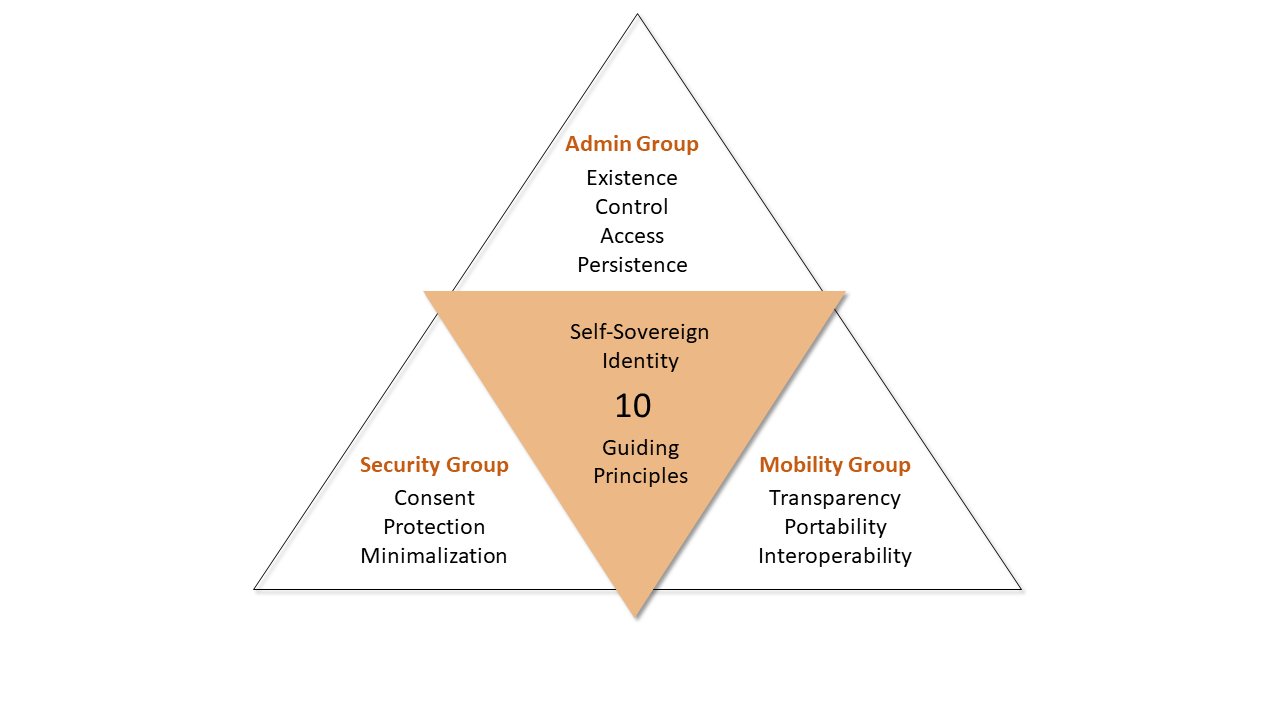
Admin/Control Group
After a user registers the digital identity, they can persistently store identities at the desired location (cryptographic wallet) of their choice, and that gives control to access their identity whenever they want and share with parties they wish to interact.

Existence
A real-world existence is required for any digital identity to be created. In addition to foundational identities, a person may have additional digital identities called persona, for example, professional identity, student identity, gamer identity, dating identity etc.
Control
Users must have full control over their identities. Users can make a choice to keep their identity available for public or private.
Access
Users must have access to their data - all claims and attributes or properties associated with the identity. Identity wallets host this digital data and available for access by the user's private key.
Persistence
Identities must remain persistent long enough, preferably forever. At the same time, some of the jurisdictions (GDPR/CCPA) mandates a right to be forgotten user's digital identities allowing users to dispose of their identity.
Security Group
The digital identity can be used to access services online, including social, health, legal, banking etc. Who can access the information, and what attributes or properties are exposed can be defined by the security group.

Consent
Users must agree or provide permission to access the user of their identity. The consent must be explicit to the first layer (recipient of the consent) and not implicitly transferable to the second layer (vendors and customers of the recipient).
Protection
The rights of users must be protected. The freedoms and rights of a user must always be protected, and the network should default to it to protect users from censorship.
Minimalization
Disclosure of claims must be minimized. Disclose only the minimal data required to accomplish the task. If age is needed, do not disclose the birthdate.
Mobility Group
The user identity and claims move across the Internet. It requires the involved entities able not only to handle this information transparently but also to interoperate with open standards.

Transparency
Systems and algorithms must be transparent. They must be free, open-source, assessed, audited and self-sufficient without further non-free software dependencies.
Portability
Information and services about identity must be transportable. Users must be able to switch to different jurisdictions, networks or service providers with their identity and claims.
Interoperability
Identities should be widely usable across any jurisdiction, geographical boundaries or varied service providers and applications.
Organization Identity
The above guiding principles are architected to preserve individual privacy. However, while developing the specification for decentralized Identifiers, W3C has expanded the scope from people to non-individual entities like organizations and things (can be applied to software agents. or physical products)

Though an organization can be issued a digital identity, the admin control remains with individuals of that organization to act on behalf of the organization. Let's revisit guiding principles that are different for non-individual entities.
Commission (11th principle)
The organization's identity must commission its employees by issuing a derived identity that can be used to authorize its operations and later decommission those capabilities when not needed. Currently, W3C CCG is working on authorization capabilities for Linked data. The latest draft is found here.
Existence
Though an individual identity does not be published, however, organization identity must be published by the authority that issues them. British Columbia has not only issued organization DID, but also published them here.
Control
The designated users will have full control over the organization's digital identity. The user is given the authorization to act on behalf of the organization.
Access
The designated users will be able to access the identity claims. An organization may choose to provide certain public information through its digital identity, i.e., organization address, phone number, issued business licenses etc.
Persistence
A right to be forgotten is not applicable for the organizations or things. We need their identity to persist for any future reference with specific status like active, inactive, historical etc.
Consent
The authorized users of an organization will be able to provide consent on behalf of the organization.
Protection
The freedoms and rights do not apply to an organization or thing because they can be banned or sanctioned by a jurisdiction. Any identity or service provider must be able to censor such an organization or a thing.
The minimalization, transparency, portability and interoperability for non-individual entities apply to organization identity.
Summary
Now we have a firm grasp of Self-Sovereign Identity Guiding principles that have been broken down into admin, security and mobility groups for individual digital identities.
In the last section, I expanded these principles for non-individual identities like organizations and things and introduced the Commission principle to allow an organization identity to add/remove capabilities to their employee identities.
Actions
Read The Path to Self-Sovereign Identity by Christopher Allen.
If you are an audio-visual type of person, head to his recent talk.
All content free now. Subscribe by email so that you do not miss any article.
This post and the information contained herein is provided for informational and discussion purposes only.


